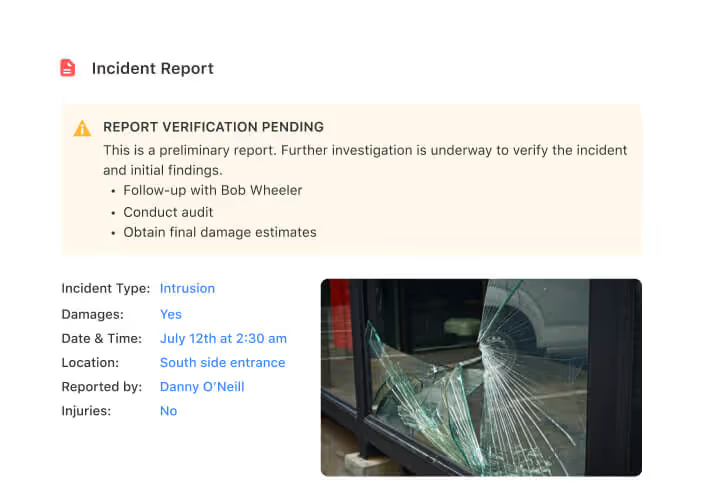
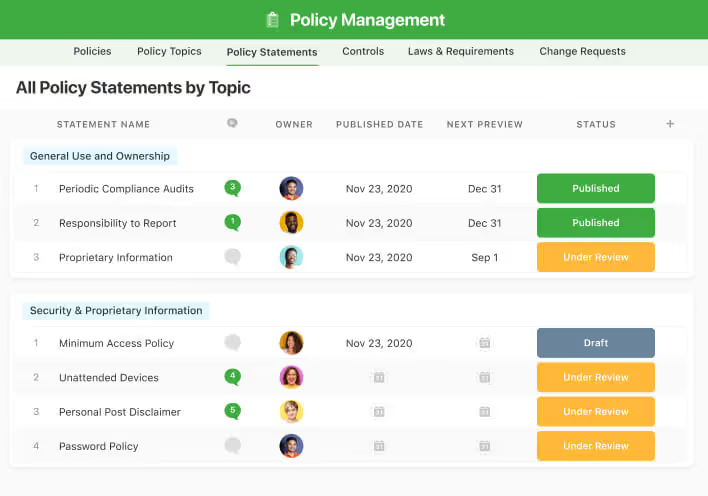
Security Operations Management
Streamline Your
Security Systems.
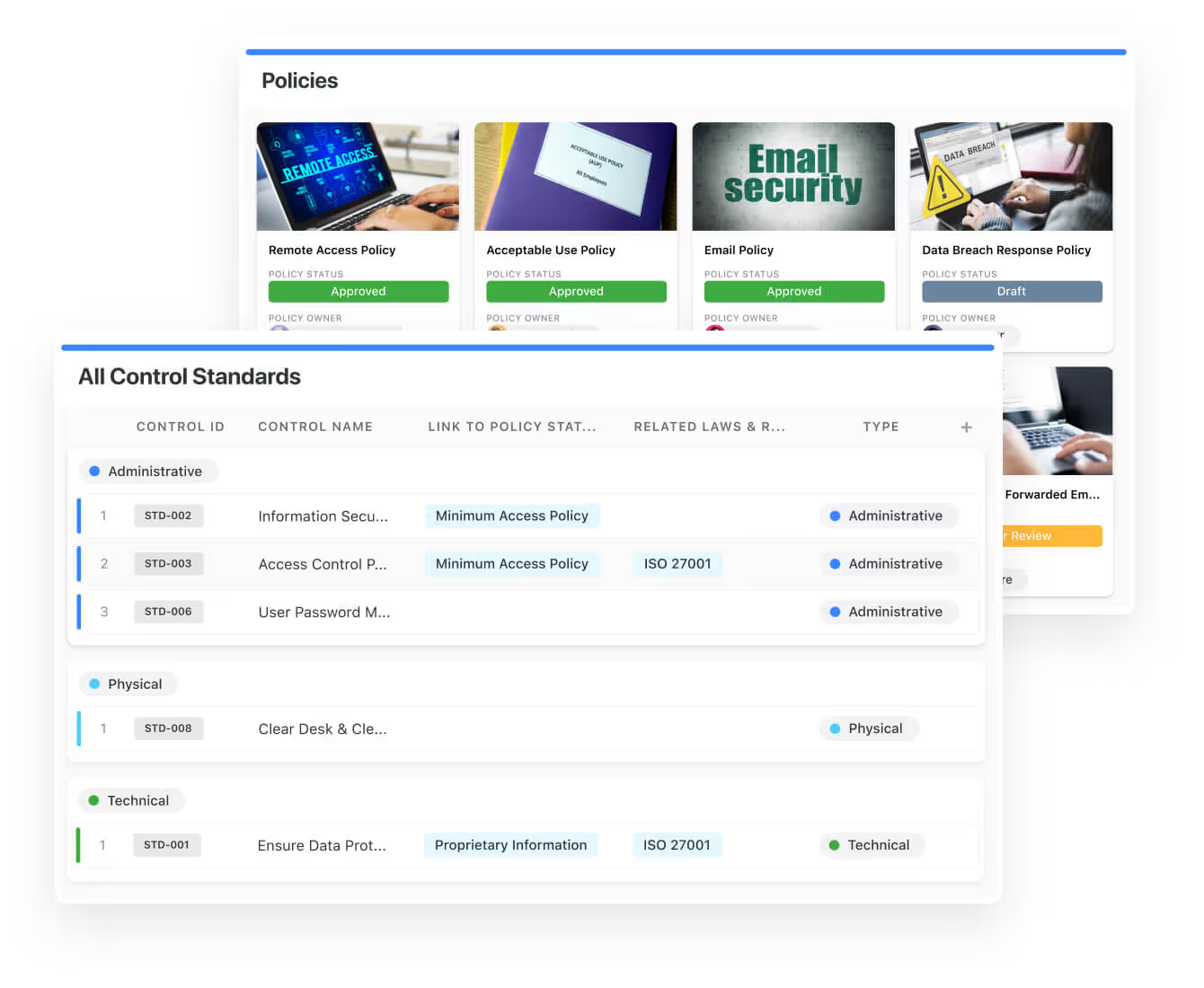
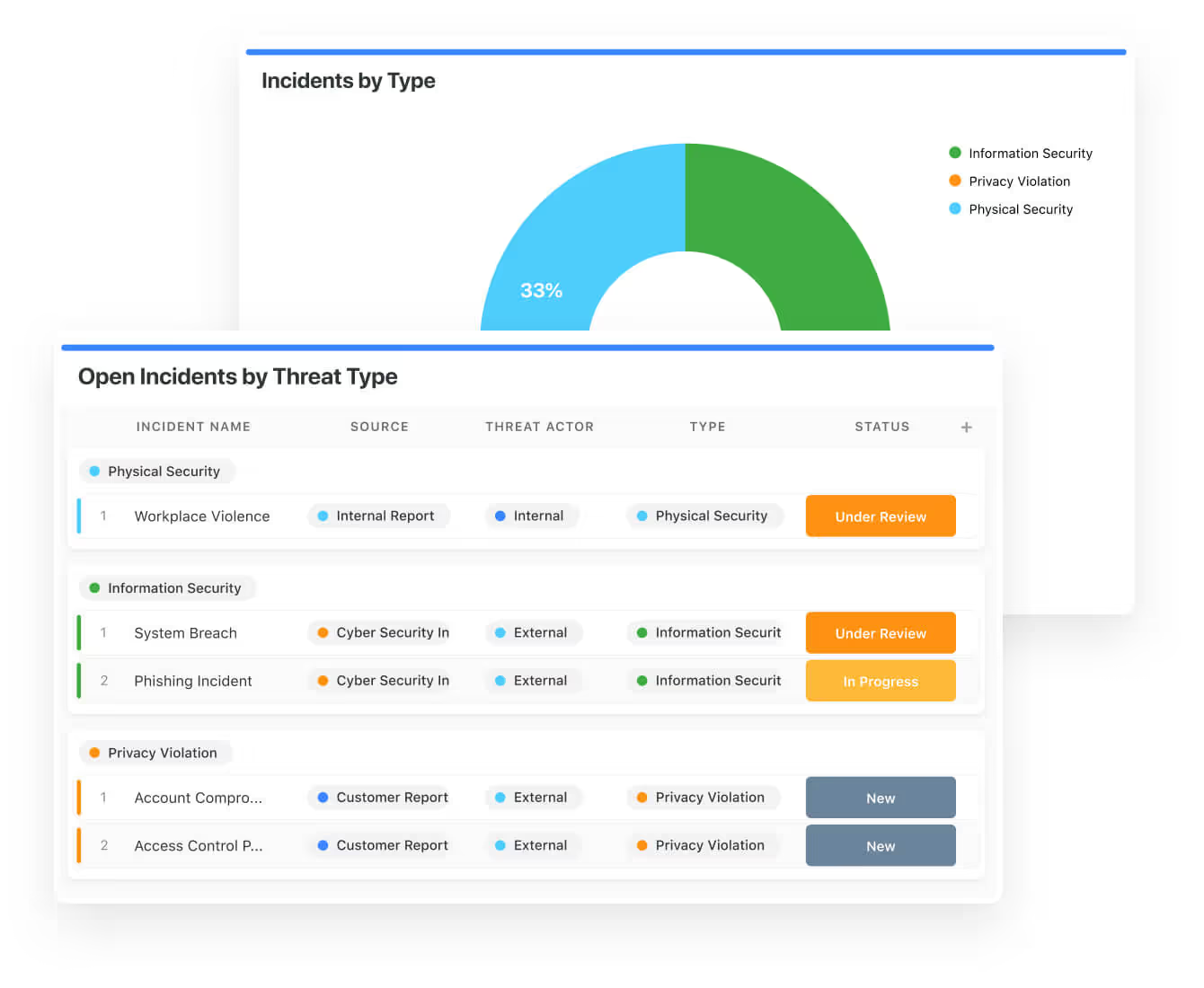
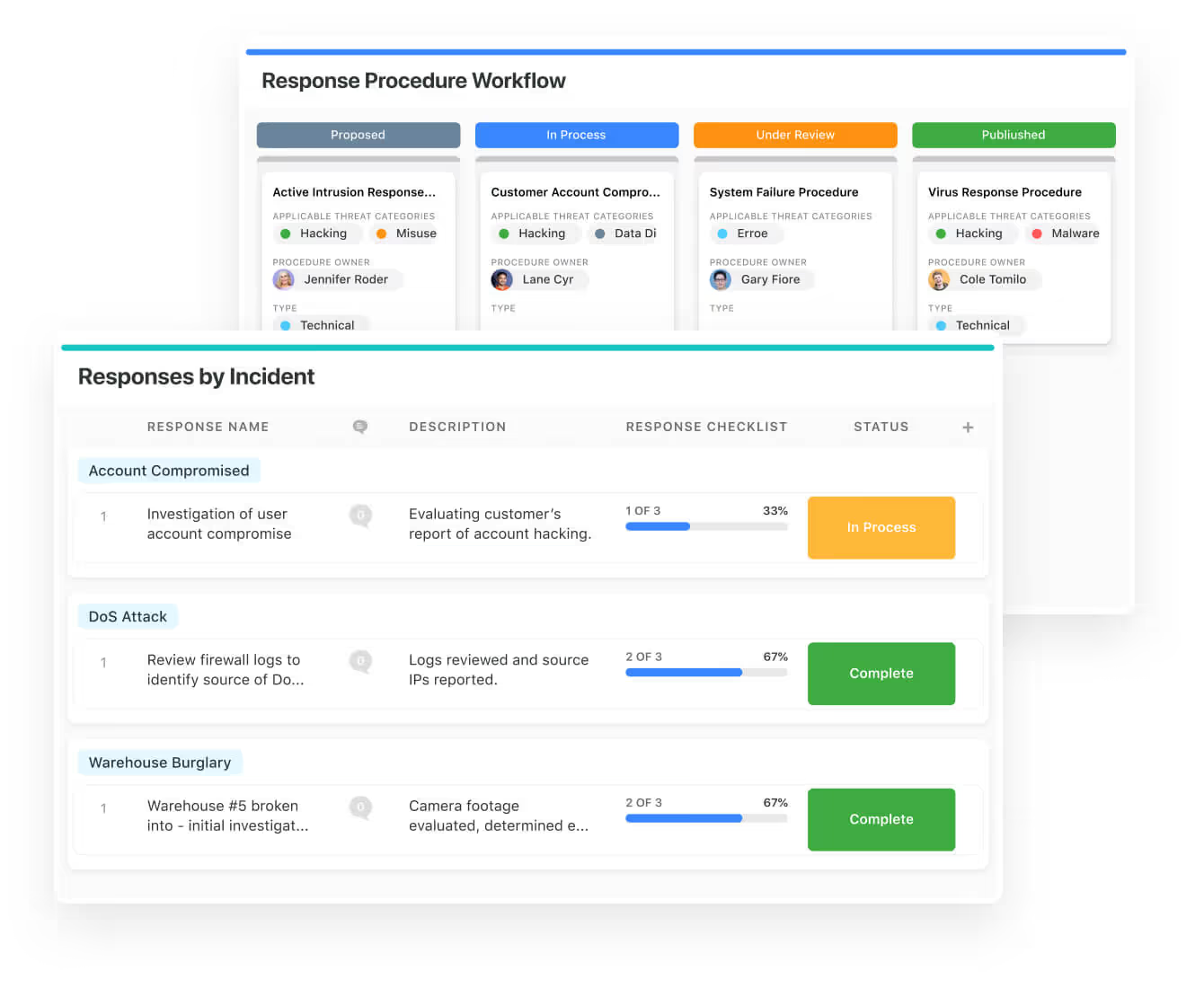
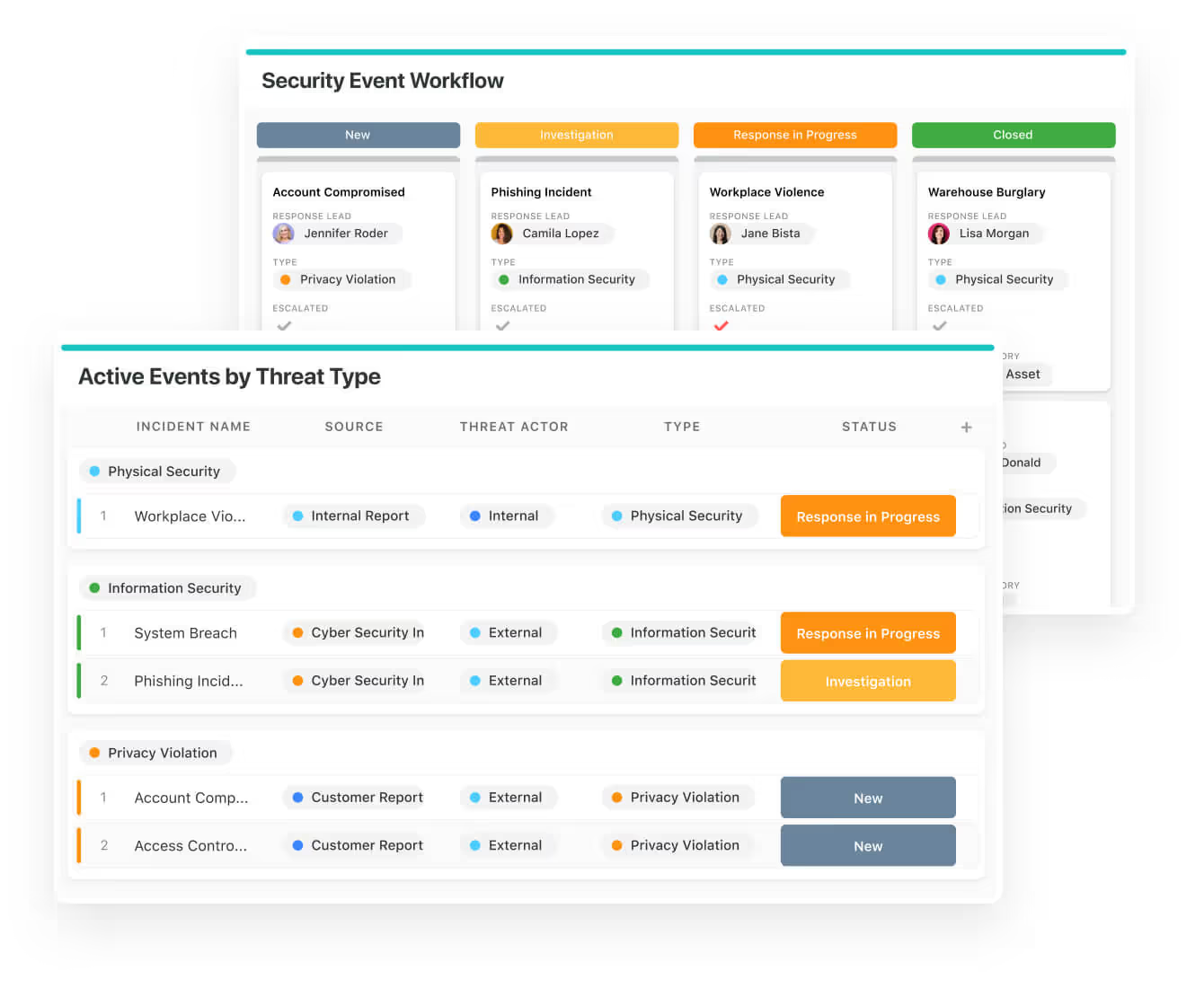
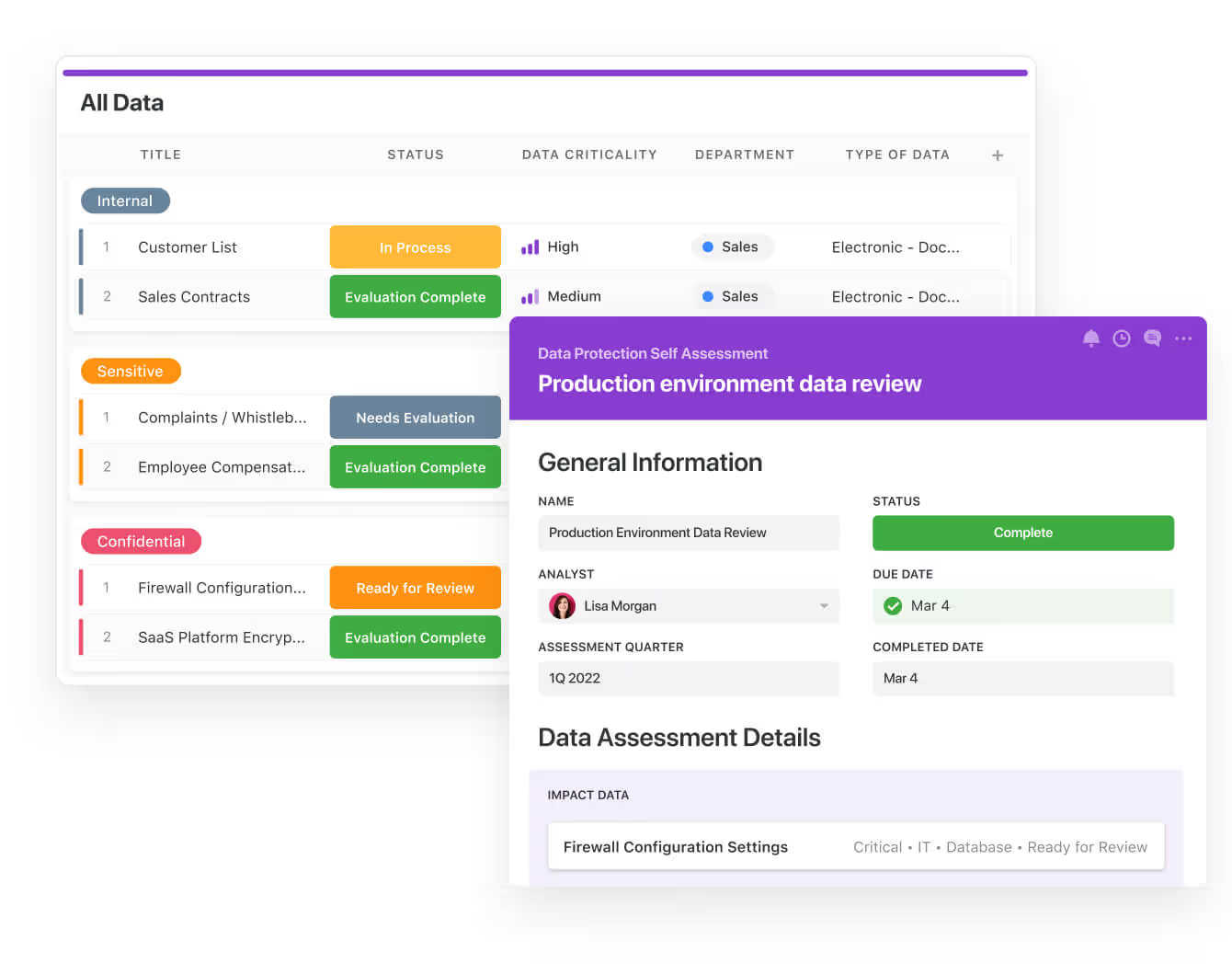
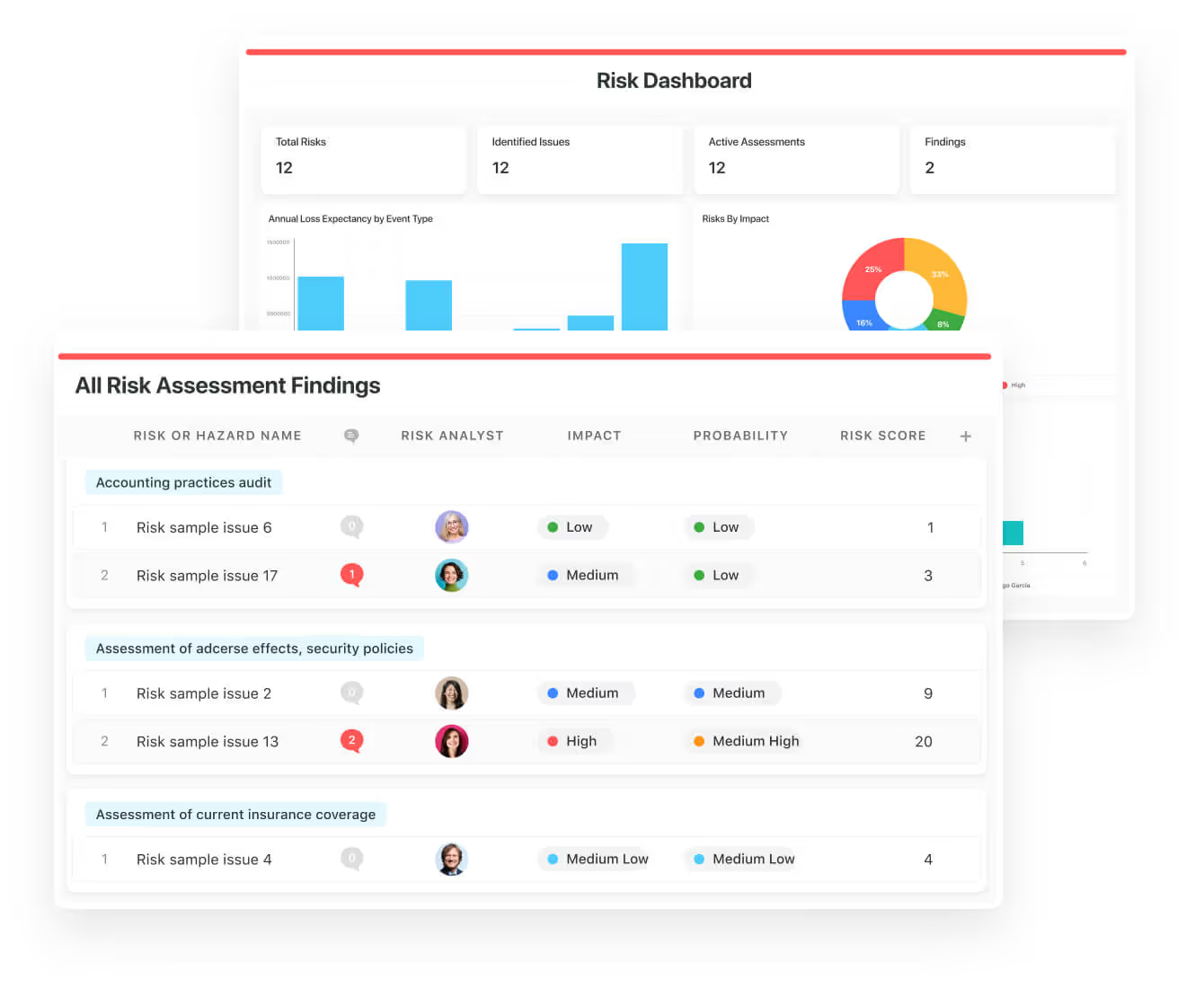
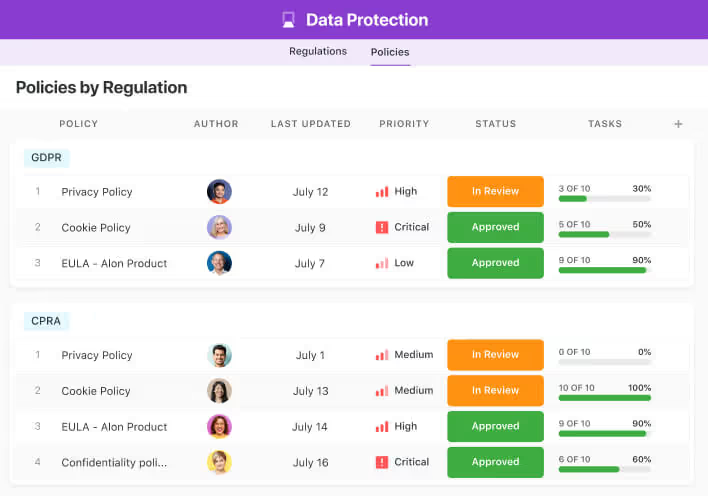
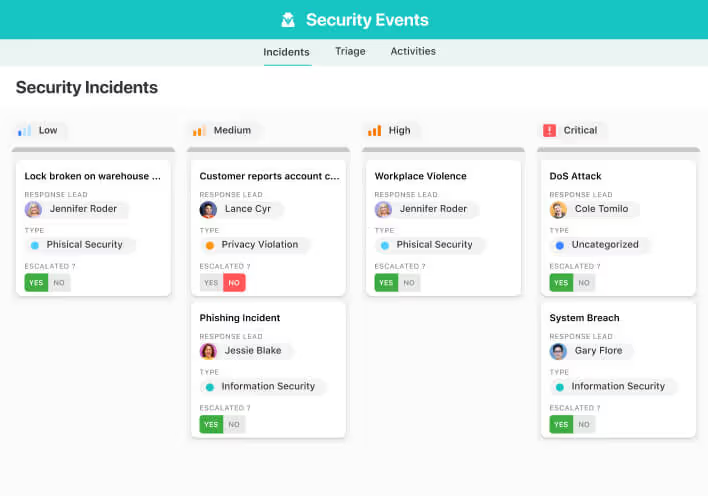
Oversee every aspect of your security operations in one place. Define objectives, record detailed procedures, and manage critical threat responses efficiently. Track intelligence, assess organisational risks, and implement coordinated action plans to stay fully prepared.

Getting Started is Simple
3 Steps to Smarter, More Efficient Business.
1. Share What You Need
Tell us about the process, workflow, or part of the business you want to improve. In a short call, we understand your goals and what the system needs to achieve.
2. Get Your Plan
We map the process and show how systems, automation, and AI will remove manual work and improve performance.
3. We Build and Deliver It
We create your system with the right mix of structure, automation, and AI support so it works smoothly from day one, increases capacity, and helps your business grow.
Review Examples